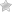If WordPress suddenly sends spam, this can be the simple cause
WordPress and other content management systems must be able to send e-mails. However, this also entails dangers. A practical example shows: Even without a hack, a WordPress installation can easily become a spam catapult and damage the reputation of the IP addresses and domains involved.
Sending spam through WordPress: That happened
The web server on which the WordPress installation in question is located is well secured and not infected by malware. All sites and applications on the server send e-mails via the Amazon SES service, which acts as a smart host or SMTP gateway. Suddenly, it caught the eye: The proportion of bounces (undeliverable e-mails) and complaints (users or providers report spam) in relation to all e-mails sent increased significantly.
This problem had to be analyzed and solved. By default, Amazon SES does not provide any information about which e-mails from which domain lead to bounces and complaints. Only an overview is available to the owner of the SES account. Total number of messages, rejects, bounces and complaints are displayed on the timeline:
Amazon SES Rejects, Bounces, Complaints
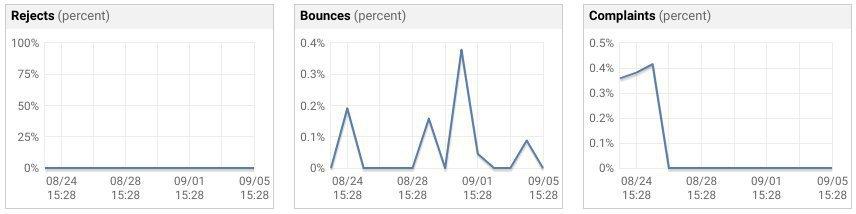
In order to identify the cause of the problem, the account holder has to subscribe to notifications per domain. He configures a so-called SNS Topic for this purpose.
Amazon SES Notification Topics
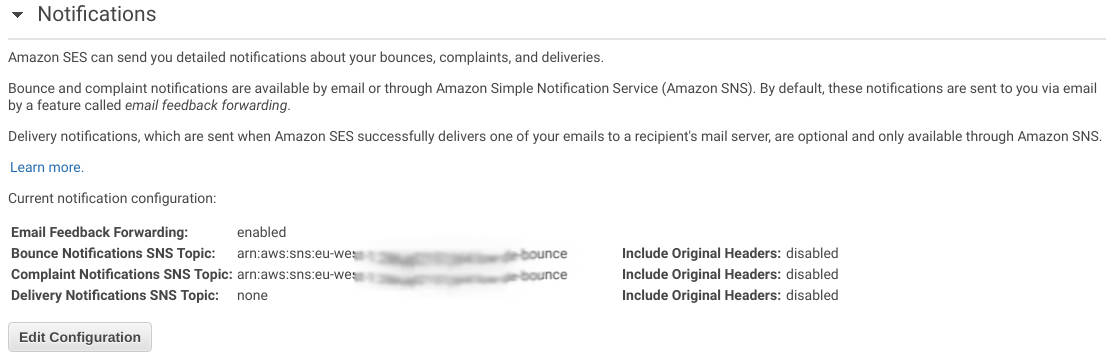
Result: Rejects, bounces or complaints are reported to the owner in the desired way, for example by e-mail in JSON format.
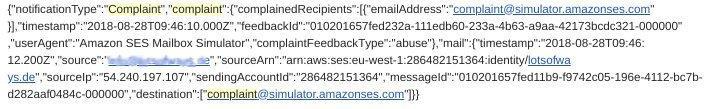
Amazon-SES-Complaint-Notification
Clear advantage: As the owner of the Amazon SES account, we now know which domains are responsible for the increased spam volume. In the next step, the analysis continues. Is the amount of spam generated by the hosting customer directly in the e-mail client or on the workstation that sends it via SMTP? Or is the WordPress installation on the web server to blame, for example, because it was hacked?
[/card] [card title="Impending Danger" text="text-darken-3 grey" title_color="blue"] When it comes to email deliverability, the reputation of the sender IP and sender domain are relevant. If spam messages are repeatedly complained about among your senders, you damage your reputation and risk that the deliverability of your legitimate messages decreases.
[/card][card title="How can I further Reduce Spam?" text="text-darken-3 grey" title_color="blue"] Configure your email domain strictly by using SPF, DKIM and DMARC and make your DMARC policy more restrictive step by step. In this way, you effectively prevent third parties from successfully sending spam on your behalf in other scenarios not addressed in this article. Messages are then rejected directly by the receiving server if they are not legitimate, without interaction with the recipient and thus a spam complaint. However, the integration of a strict DMARC policy requires experience and close monitoring. If it is too strict or incorrect, e-mails will be lost.[/card] [card title="Help needed?" text="text-darken-3 grey" title_color="blue"] Every month we send a large number of legitimate emails to customers with a strong reputation focus and are happy to help with email deliverability and sender reputation. Please do not hesitate to contact us!
[link text="blue" to="/contact/"]Contact[/link] [/card]
Analysis of the e-mails sent by WordPress
The plugin “WP Mail Logging” does a good job in root cause analysis on the WordPress level.
It performs the simple task of logging all e-mails sent by a WordPress installation in tabular form. After WP Mail Logging has been installed and activated, a functional test is recommended, for example by triggering a password reset mail. If everything fits, we now have a functioning control system. It is supposed to tell us whether malicious software sends e-mails from our WordPress installation. A parallel malware scan is recommended, for example with WordFence or the Sucuri scanner. Sucuri also offers a nice guide to clean infected WordPress websites.
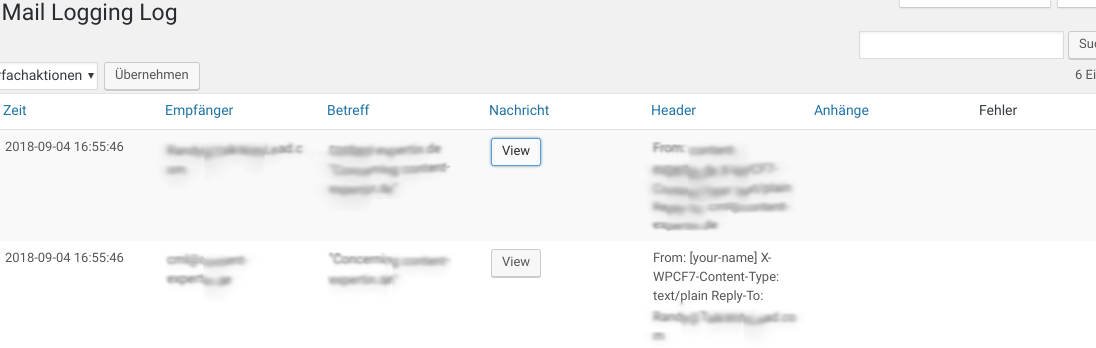
WP-Mail-Logging-Overview
The next step is to wait and see – as long as the admin does not find an acute infection of the WordPress website, which would also explain the unwanted sending of e-mails.
In our current case, the analysis actually led to a result: the contact form was to blame. The website operator had insufficiently protected his form from spam entries and had also configured an automatic acknowledgement of receipt. Spammers could thus enter any sender addresses in the contact form. The automatic acknowledgement of receipt was sent to the contact form via WordPress, web server and Amazon SES as gateway.
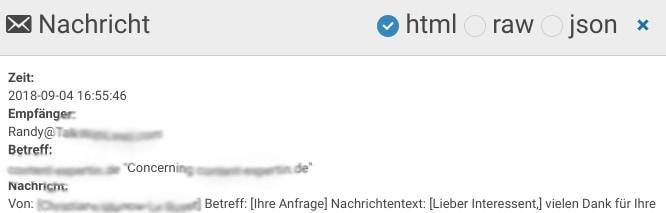
[/card]